Enabling Chroot-Style Isolation for Users in CoreSSH Server
Requirements: CoreSSH Server
CoreSSH Server is a secure, high-performance SSH server that provides SFTP, SCP, and shell access on Windows. It enables users to connect and upload or download files, manage remote resources, and interact with remote systems.
Introduction
Chroot-style isolation in CoreSSH Server refers to the practice of limiting a user's view of the filesystem to a designated root directory, effectively "jailing" them within a restricted environment.
This enhances security by preventing users from navigating outside their assigned directory structure, even if they attempt to use relative paths or symbolic links. CoreSSH Server achieves this through user-specific directory constraints.
In this article, we’ll explain how to configure and validate chroot-like isolation using CoreSSH’s built-in directory controls.
Configure
To enable chroot-style isolation for a user in CoreSSH Server, the only required step is to specify a custom root directory in the user configuration. This should be all that is necessary for most scenarios.
This is done by navigating to the Edit User page in the CoreSSH admin console. Ensure that the "Use Default Root Directory" checkbox is unchecked—this setting is disabled by default, meaning users are already restricted to the path you define.
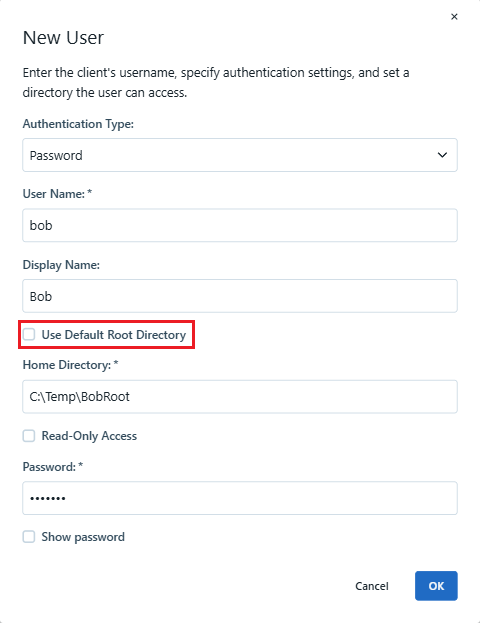
In the "Home Directory" field, enter the absolute path to the folder you want the user to be confined to. This directory becomes the user's virtual root, and they will not be able to traverse outside of it during their SFTP session.
Once you are done click "OK" and this configuration takes effect immediately.
We appreciate your feedback. If you have any questions, comments, or suggestions about this article please contact our support team at support@nsoftware.com.

