Getting started with SSH Reverse Tunnels In PowerShell Server
Contents
Overview
SSH Reverse Tunnels provide a way to allow connections to network resources that would not typically be available. For example, a device behind a firewall that would typically be unavailable to the outside world can be accessed through an SSH Reverse Tunnel. The client connects to the publicly accessible port on the SSH host and traffic is forwarded to the endpoint inside the network protected by the firewall.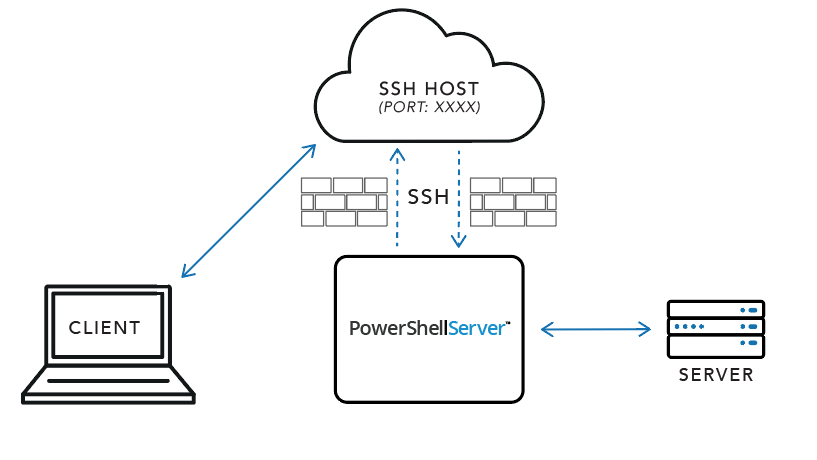
In the above diagram, assume that PowerShell Server and the host identified by Server are on the same network, isolated from the Client. SSH Host is publicly accessible, and accessible by the Client. For the sake of clarity, assume that Port XXXX is 7777, but any open port may be used.
PowerShell Server connects to a SSH Host and requests that the incoming traffic on Port 7777 be forwarded back to PowerShell Server, which will then be directed to Server. Once this tunnel has been established, Client will then be able to connect to SSH Host on Port 7777 in order to communicate with Server.
Creating an SSH Reverse Tunnel
The Tunnels tab allows for the creation of SSH Reverse Tunnels through a simple interface:
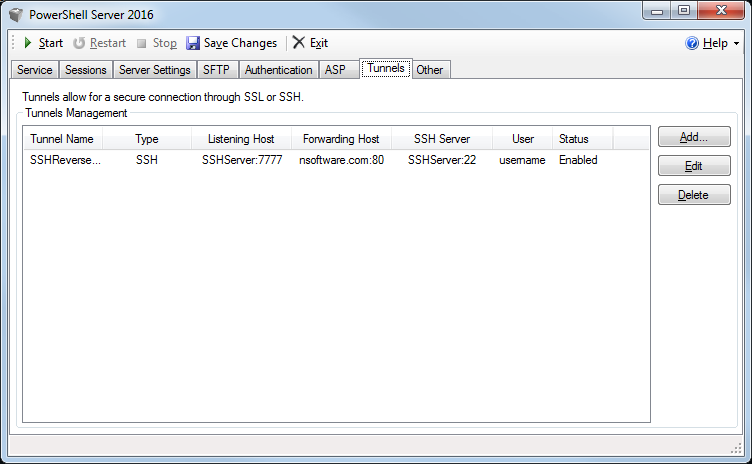
The tunnels list provides some information about existing tunnels:
- Tunnel Name provides a friendly name for the tunnel.
- Type indicates the type of tunnel. Plaintext, SSL, and SSH Reverse Tunnels are supported.
- Listening Host indicates where the tunnel is listening.
- Forwarding host indicates where the tunnel is directing its traffic.
- SSH Server is the SSH server that PowerShell Server will connect to in order to establish the SSH Reverse Tunnel.
- User is the username PowerShell Server will use to authenticate to the SSH server.
- Status indicates whether the tunnel is Enabled or Disabled.
Clicking the Add... or Edit buttons will present a form that can be used to create a new tunnel, or edit an existing one, and clicking Delete will remove the selected tunnel.
To create a new SSH Reverse Tunnel, click Add... in the Tunnels tab. This will present the following form:
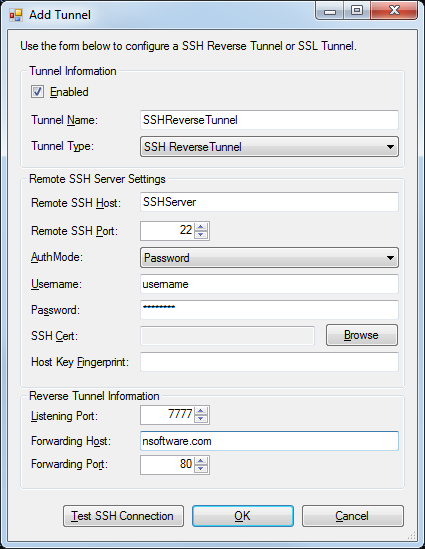
- Enabled indicates whether the tunnel should be active or not.
- Tunnel Name provides a friendly name for the tunnel.
- Tunnel Type indicates the type of tunnel. Plaintext, SSL, and SSH Reverse Tunnels are supported. This guide only covers SSH Reverse Tunnels.
- Remote SSH Host is the SSH server that PowerShell Server will connect to in order to establish the SSH Reverse Tunnel.
- Remote SSH Port is the port on which communication with the SSH server will take place. Most servers use port 22, which is the default value.
- AuthMode is the type of authentication that will be attempted when logging in to the server. Password and Public Key authentication are supported.
- Username is the username PowerShell Server will use to authenticate to the SSH server.
- Password is the password PowerShell Server will use to authenticate to SSH server during Password authentication.
- SSH Client Key is the certificate PowerShell Server will use to authenticate to the SSH server during Public Key authentication.
- Server Fingerprint indicates the SSH host key fingerprint of the server. This value is read-only and purely informational.
- Listening Port indicates the port on which the SSH server will listen for the tunneled traffic.
- Forwarding Host is the host where the tunneled traffic will be forwarded.
- Forwarding Port is the port on which the tunneled traffic will be forwarded.
Once the necessary information has been entered, the Test SSH Connection button may be used to test the connection to the SSH server in order to verify the validity of the information provided.
Using an SSH Reverse Tunnel
Once the SSH Reverse Tunnel has been added to PowerShell Server, click Start in the toolstrip at the top to start the server and establish the SSH Reverse Tunnel. Once started, the endpoint can be reached by connecting to Listening Host. In the case of this example, where the endpoint is a web server, the browser can be used to navigate to SSHServer:7777 in order to view the nsoftware.com webpage.
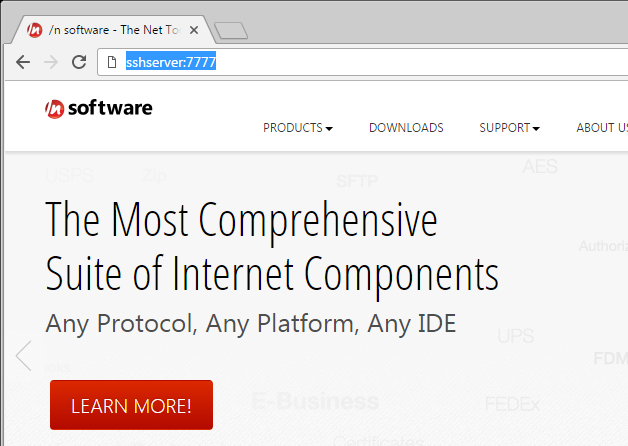
Note that the SSH Reverse Tunnel simply forwards TCP traffic, so this method could be used to access a variety of protocols. This example demonstrates using the tunnel to access a web page over HTTP, but this method could easily be adapted to access SSH, SFTP, or other servers.
We appreciate your feedback. If you have any questions, comments, or suggestions about this article please contact our support team at support@nsoftware.com.

